Is there anything more terrifying to a publisher than the prospect of having all their hard work destroyed by a malicious hacker?
Hackers may intend to steal your data or mess up your website’s layout. They may also use your server as an email relay for spam or set up a temporary webserver to serve malicious files. In this article, we provide ten concrete tips to protect your website from hacker attacks.
How do websites get hacked?
Can you tell the difference between a hacked website and an ordinary website that’s performing poorly? Before you learn how to stop hackers from gaining control, it’s probably a good idea to first discuss how a website can be hacked.
There are numerous types of website hacking attacks, but we’ll explain the most common hacking techniques:
• Ransomware hack
Ransomware is a malware attack that encrypts a victim’s files. The hacker responsible for releasing this malware demands a “ransom” from the victim in exchange for restoring access to these encrypted files.
The victims are often directed to a web page to pay a fee( the ransom) to obtain the decryption key. The ransom runs up to thousands of dollars for a small website and millions for corporations.
• Gibberish hack
The purpose of a gibberish hack is to take advantage of a legitimate website’s good standing with Google to drive traffic to another website. The gibberish hack automatically creates numerous pages on your site with nonsensical sentences stuffed with keywords. These pages contain URLs that may entice visitors to click them. When visitors click on the URLs, they are redirected to an unrelated page, such as a pornographic website.
• Cloaked keywords hack
The Cloaked keywords Hack generates many pages with nonsensical text, links, and images automatically. Because these pages often contain basic template elements from the original site, they may appear like standard sections of your website until you read the altered content.
The hacked pages are created with the express purpose of manipulating Google’s ranking factors. Hackers frequently attempt to profit from this by selling the links on the hacked pages to various third-party vendors.
• Distributed denial of service (DDoS)
A Distributed Denial-of-Service (DDoS) attack attempts to bring a computer or network to a halt, rendering it inaccessible to its intended users. DDoS attacks achieve this by flooding their target with traffic or sending information that causes the crash. In both cases, the DDoS attack denies legitimate users (i.e., employees, members, or account holders) access to the service or resource.
• Code injection hacks
Code injection is a broad term that refers to attacks that involve the injection of malicious code into computer systems. These types of attacks are possible when input or output data is not validated properly.
Once an attacker successfully injects their code into the system, they can jeopardize the system’s integrity and security. Additionally, hackers launch more dangerous hacks, as the system is already infected and becomes vulnerable.
• Brute force attacks
In this hacking technique, the attackers attempt multiple password combinations until one of them matches. This type of hack is easy to implement in its implementation, but it requires a significant amount of computing power. The longer your password, the more difficult it will be to gain access via brute force. At times, attackers will also make use of dictionaries to expedite the process.
• DNS spoofing
Attackers can force victims to visit a bogus website by using DNS spoofing attacks. Hackers change the IP addresses stored in your website’s DNS server to malicious IP addresses that lead users to their website.
How to protect your website from hackers
1. Install an effective firewall
Hackers don’t break into websites manually. A skilled hacker will create a bot that automatically scans the web for vulnerable websites and does most of the work. Although bots are programmed to perform precise tasks, they are not sentient.
A firewall is essentially a piece of code that detects malicious requests. Each information request made to your website is routed through the firewall. Suppose the firewall determines that the request is malicious or originated from a known malicious IP address. In that case, the request is blocked rather than processed.
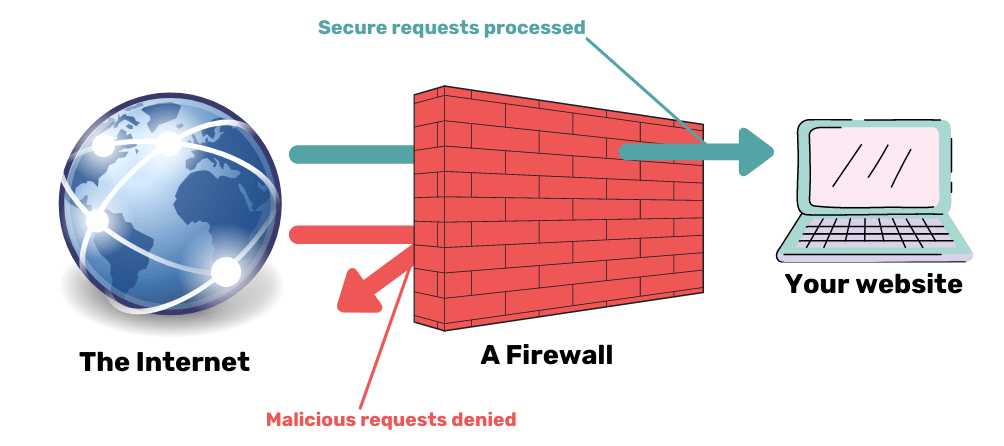
Some firewalls allow for user configuration. However, unless you are a professional web security expert, we do not recommend it. Firewall rules are developed following extensive security research and active malware removal.
For example, most WordPress security plugins include rules that prevent users who do not have administrator access from accessing the wp-config.php file. The wp-config.php file is a critical component of WordPress and contains a great deal of sensitive information. As a result, the firewall examines each request to the website to determine if it includes the text “wp-config.php.” If that rule is triggered, the firewall denies the request.
Additionally, hackers attempt to hack as many websites as possible after discovering a vulnerability, and they expose their IPs in the process. WordPress firewalls monitor and block malicious IP addresses in advance of these attacks. No firewall is completely impenetrable, but it is better to have one than none at all.
2. Create a strict password policy
Hundreds of thousands of websites use easy-to-guess passwords. Hackers maintain a database of such passwords known as a rainbow table. Then they launch a ‘dictionary attack’ using these tables. Hackers can combine dictionary attacks with brute force attacks to increase their chances of success.
We recommend that you use long, strong passwords that contain a combination of letters, numbers, and symbols. Uncommon combinations are difficult to crack and can take years to decode using brute force algorithms.
3. Enable HTTPS by installing an SSL certificate
Hypertext transfer protocol secure (HTTPS) is a secure HTTP — the primary protocol for transmitting data between a web browser and a website.
HTTPS increases the security of data transmission. This is especially critical when users transmit sensitive information, such as when they log into a financial service, email, or other sensitive websites.
A Secure Sockets Layer (SSL) certificate is a security protocol that encrypts all communication between a website and its visitors. By implementing one, you can ensure that even if a hacker intercepts data from your website, they will not decipher this data.
4. Protect your website by keeping an activity log
Observing unusual activity on your website can help you notice an incoming hack attack in some situations. Someone else could create an administrator account or deactivate a security plugin without your consent.
While these are all legitimate website administrator actions, they also indicate unauthorized access. Activity logs inform you of what is happening on your site, allowing you to determine whether or not these actions are legitimate.
The majority of hackers are very cautious to avoid detection, as they can only control your website for as long as they avoid detection. Activity logs help you notice changes, allowing you to detect any unauthorized activity quickly.
5. Update your software regularly
A significant percentage of hacks occur due to hackers identifying a vulnerability in a theme or plugin and exploiting it across multiple websites. Themes and plugins are both types of software — lines of code that will invariably contain bugs. Some bugs are relatively harmless and may only cause a minor hiccup during an update. Others can make the website’s code exploitable.
When the developers release a fix, a new update is announced to the general public. If you fail to install the update, your website could fall victim to hackers looking to make a quick buck by exploiting the bugs in old patches.
6. Implement two-factor Authentication
Two-factor authentication (2FA) is a security tactic that requires you to have access to an additional device or token in addition to your password to log in.
There are several protocols for two-factor authentication, including TOTP (time-based one-time password) and HOTP (HMAC-based one-time password).
Several paid and free apps enable you to add two-factor authentication to your login page. If your website has many contributors, you must implement two-factor authentication to safeguard its access.
7. Maintain routine backups
Making backups is one of the most undervalued strategies you can employ. Always make daily backups of your website to ensure that you can quickly restore it in the event of a catastrophic failure or hack.
Select a reliable backup software because manual backups can be challenging to perform correctly without considerable expertise.
8. Choose a reputable web host
Most publishers and webmasters hold web hosts accountable for even the website’s security. However, if your website is hacked, it is rarely the host’s fault. However, the possibility of a web host security breach remains. We recommend that you seek out the most secure hosting service available.
9. Disable automatic commenting
As a publisher, nothing could be more satisfying than hitting publish on your website and immediately seeing comments begin to pour in? It indicates that people have visited and interacted with your content.
Comments are an excellent way to track engagement, demonstrate social proof to other visitors, connect with others in your niche, and even accept constructive feedback.
However, there will always be spammy comments that are undesirable — bots or fake traffic, phony accounts, and hackers waiting with a spammy link. At the very least, it’s inconvenient; at worst, it poses a security risk to you and your users.
If users can post comments directly to your website, malicious links may infiltrate the comments section. This is especially dangerous for your website’s visitors, who may click on the link and risk exposing personal information or installing malware unintentionally.
To combat this, you can configure your site’s settings to require manual approval of comments before they appear on your website, allowing you to remove any spam.
You can also use an anti-spam program or plugin (such as Akismet for WordPress users). You can also request that visitors register before being able to leave a comment.
10. Defend against cross-site scripting (XSS) attacks
With Cross-site scripting (XSS) attacks, hackers inject malicious JavaScript into your web pages. These JavaScripts run on your users’ browsers, altering the page’s content or stealing data for the hacker.
For instance, if you display comments on a blog article without validating them, a hacker can submit comments containing script tags and JavaScript. The malicious scripts steal the user’s login cookie, allowing the hacker to access user accounts interacting with the comment.
This technique is especially relevant in modern web applications, where web pages are constructed using user content and generated HTML.
Fortunately, you can avoid the technical jargon by installing or using Content Security Policy (CSP) software. CSP is a header that your server returns, instructing the browser to restrict how and what JavaScript is executed on the page.
Other tips to protect your website from hackers
Partner with reputable ad networks
When you put ads on your website, you must ensure that your traffic and inventory are protected from malvertising and abusive content. Though this is not about hacker attacks, it involves a publisher’s reputation and revenue stream.
Always check if your Ad Network provides you with anti-malware solutions and security tools.
Adsterra has been evolving its in-house solutions paired with third-parties tools since 2013. We monitor ad inventories 24/7, with both algorithms and human assistance. Reach out to us if you suspect any malicious ad activity on your website. All publishers get 24/7 help from our support team via live chat.
Conclusion: Why should your website be secured against hackers?
Your website is valuable and probably a significant source of revenue. Hackers may not financially benefit from attacking your website. However, they could use it for a far more dangerous hacking campaign. Therefore, having a small website does not exclude it from malicious intent.
It is also vital to safeguard your users’ data and identities. By visiting your website and accepting cookies, they are expressing a certain level of trust. You don’t want to betray your users’ trust by managing a vulnerable website.
By remaining vigilant, you can stop any incoming hack before it occurs. Protecting your website from hackers is a continuous process. You can take specific steps once, but you must constantly monitor the news for new threats.
